How Secure Is Your Android Unlock Pattern?
 All of us have (or should have) seen the screen in the Android Settings listing the various methods for unlocking your device. It varies from one device to another but there are a few constants. My Galaxy S5 shows the following options: Swipe, Pattern, PIN, Password and Fingerprint. I’ve had other devices in the past that include Face and Voice unlock options as well. Each option lists the level of security that the unlock method gives you. With some recent findings Samsung and Google may be forced to update the Pattern level of security from “medium security” to “low to medium security”.
All of us have (or should have) seen the screen in the Android Settings listing the various methods for unlocking your device. It varies from one device to another but there are a few constants. My Galaxy S5 shows the following options: Swipe, Pattern, PIN, Password and Fingerprint. I’ve had other devices in the past that include Face and Voice unlock options as well. Each option lists the level of security that the unlock method gives you. With some recent findings Samsung and Google may be forced to update the Pattern level of security from “medium security” to “low to medium security”.
Marte Løge, a technology analyst with Itera ASA and a recent graduate of the Norwegian University of Science and Technology, conducted a study of 3,400 individuals and their unlock patterns as part of her master’s thesis.
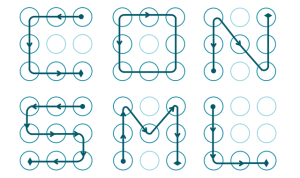 She discovered that 77 percent of all participants unlock patterns started in one of the four corner nodes. 44% of the participants unlock patterns started with the top left node. The majority of the patterns went from left to right and or top to bottom. More than 10% were representative of a letter in the alphabet, which was often an initial of someone close to the participant such as a spouse or child.
She discovered that 77 percent of all participants unlock patterns started in one of the four corner nodes. 44% of the participants unlock patterns started with the top left node. The majority of the patterns went from left to right and or top to bottom. More than 10% were representative of a letter in the alphabet, which was often an initial of someone close to the participant such as a spouse or child.
Android allows for unlock patterns to have a minimum of four nodes and a maximum of nine nodes. This allows for a total of 389,112 different combinations of nodes that can be used in a given unlock pattern.
On average most users had patterns that were made up of five individual nodes which limits the possible combinations of patterns to less than 9,000. A large percentage of the study members only used four nodes which limited the combinations down to 1,624.
Marte was interviewed by Ars Technica at PasswordsCon in Las Vegas and stated,”Humans are predictable, we’re seeing the same aspects used when creating a pattern locks [as are used in] pin codes and alphanumeric passwords.”
With all the news lately about data breaches and compromised accounts it has become more and more obvious that we need to be more security conscious and not just with our usernames and passwords. When protecting our data and our privacy we can’t use easy to guess methods and have to make them more complex. A good rule of thumb is that if it is frustrating for you to enter it every time it is ten times more frustrating for someone to guess or crack it.
Bruce Schneier says in his book Secrets and Lies, “People often represent the weakest link in the security chain and are chronically responsible for the failure of security systems.” Let’s all do our part to make our own data more secure and avoid making it easier for others to access our data without our consent.
Source Link: Ars Technica




