Android 5.x Password Lockscreen Bypass Vulnerability
 There have been a lot of security related items in the news recently, everything from Ashley Madison, to Stagefright, lockscreen pattern vulnerability, Lockerpin and more! Today we can add one more item to the list. Researchers at the University of Texas discovered a new vulnerability relating to Android 5.x (up to 5.1.1) and the password lockscreen. The vulnerability only affects those using a password lock and does not impact those using patterns or a pin number.
There have been a lot of security related items in the news recently, everything from Ashley Madison, to Stagefright, lockscreen pattern vulnerability, Lockerpin and more! Today we can add one more item to the list. Researchers at the University of Texas discovered a new vulnerability relating to Android 5.x (up to 5.1.1) and the password lockscreen. The vulnerability only affects those using a password lock and does not impact those using patterns or a pin number.
When testing the researcher only attempted the vulnerability on Nexus devices, I attempted it on my Samsung Galaxy S5 and was unable to replicate it. The vulnerability was reported to Google in June and was patched earlier this month. Some devices may still be at risk if they have not been updated or the manufacturers or carriers haven’t released the patch.
The vulnerability is very easy to take advantage of and requires only that you physically have the phone in your possession and some quick steps.
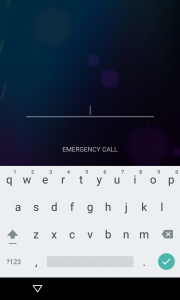
- From the locked password screen open the Emergency Dialer.
- Enter several random characters (the recommendation is 10 asterisks).
- Double-tap the characters you entered and highlight them.
- Tap once in the number field and press paste.
- Repeat steps three and four until you are no longer able to double-tap and get the copy/paste prompts.
- Go back to the lockscreen.
- Swipe left to open the camera app.
- Swipe down from the top of the screen to open the Notification Drawer.
- Select Settings (gear shaped icon). This will cause the password prompt to reappear.
- Repeat steps three and four as many times as possible. Eventually you will see SystemUI crash and the soft-buttons at the bottom of the screen will disappear and the camera app will expand to full screen.
- Wait patiently for the camera app to crash, exposing the home screen. Taking pictures with the phones hardware keys may speed up the process. If the screen turns off while waiting turn it back on and resume waiting.
- Soon the camera will completely crash and you will have unrestricted access to all apps and data.
Although the impact of this particular vulnerability is relatively limited it is still of some concern. It is refreshing to see Google acting so quickly to correct it.
For those of you who want to replicate but like me were unable to do so check out this video recorded by the researcher responsible for uncovering the password bypass vulnerability.
Source Link: University of Austin Texas Information Security Office



